Voice over Internet Protocol (VoIP) provides organizations with many advantages, including improved call quality, better scalability and mobility, and lower costs. However, VoIP is also vulnerable to unique threats such as telephony denial-of-service (TDoS) attacks, which can have devastating consequences for any business.
Blog
Windows 11 made easy: 6 Features to boost your laptop’s security and performance
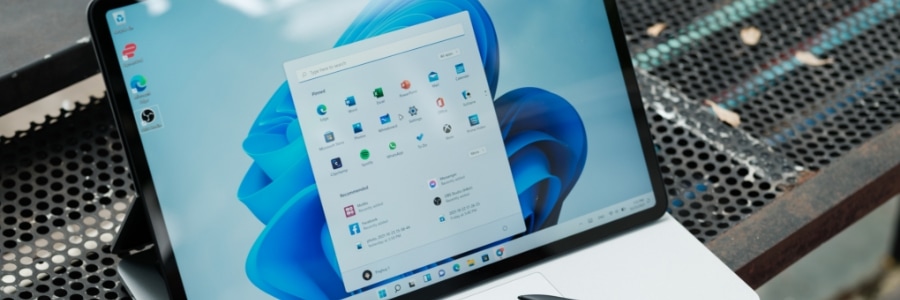
Microsoft’s latest operating system, Windows 11, brings numerous improvements compared to its predecessors. To get the most out of these improvements on your Windows 11 laptop, set up these six key features.
1. Software update settings
New laptops typically automatically check for updates, but it’s always a good idea to check manually every now and then to ensure you have the latest security patches and bug fixes.
Top 6 VoIP trends for 2024
How to boost your productivity with Microsoft Word
Revolutionizing Shopping: The AI Advantage
Nurturing Success: The Power of a Culture of Appreciation in the Workplace
2024 technology trends: What you need to know
Key Considerations When Selecting the Right Cyber Insurance Coverage
4 Questions to improve VoIP efficiency for the holidays

The holiday season brings with it an unavoidable challenge: the substantial increase in phone traffic that has the potential to overpower even the most extensive VoIP (Voice over Internet Protocol) systems. To prevent your system and employees from being swamped by the influx of customer calls, it becomes essential to optimize your VoIP system meticulously.
Disk Cleanup tool: What is it and how to use it

Keeping your computer running at peak performance is crucial to smooth business operations. Fortunately, there are plenty of methods and tools available to keep your PC in tip-top condition. One of these is Disk Cleanup, a powerful yet often overlooked solution that can give your PC a significant boost.








